ACTS 360 is an IT partner that values your time as much as you do - we prioritize your company and provide a commitment to rapid service.
Mark your calendars: October 14, 2025 - the date when Windows 10 officially reaches its end of life. After this date, Microsoft will cease to provide security updates, bug fixes, or technical support for Windows 10....
When it comes to running a business, most owners focus on elements like quality customer service, reliable products or services, and closely monitored profit and loss statements as key factors for success or failure....
Business e-mail compromise (BEC) is emerging as one of the most significant cyber threats facing businesses today. While these scams have posed challenges for organizations over the years, the advent of sophisticated...
Imagine walking into work with your team, ready to tackle the day's tasks, only to find that the Internet has gone down. Emails stop working, and productivity comes to a standstill. What would you do? For many...
As tax season approaches, businesses are busy preparing financial documents, filing returns, and meeting tight deadlines. Unfortunately, this hectic time presents an ideal opportunity for cybercriminals to strike...
Spring is here, making it the perfect time for a thorough spring-cleaning. As you declutter your office and organize your files, remember that your IT systems also need a refresh. A spring-clean for your business...
As you navigate the first quarter of 2025, it becomes increasingly evident that successful businesses are those that anticipate and adapt to the rapidly changing technological landscape. Relying on reactive IT...
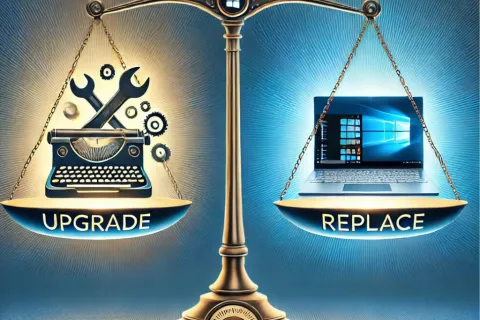
Windows 10's end-of-life is approaching, with official support ending in October 2025. This means it's time for businesses and individuals still using this operating system to make a decision. The main question is:...
National Clean Out Your Computer Day, observed on the second Monday of February, serves as a timely prompt to pay attention to your computer's health. Just as a messy desk can hinder your efficiency, a cluttered...